Beware of the Sandwich Attack: How Hackers Manipulate Blockchain Transactions
Find out how Sandwich Attacks work and what you can do to protect yourself from becoming a victim.
Sandwich Attack is a type of transaction manipulation attack that has become increasingly common in the world of blockchain and cryptocurrencies. This attack targets a specific type of smart contract on the blockchain and is designed to manipulate the outcome of a legitimate transaction. In this article, we'll take a closer look at how Sandwich Attack happens, and discuss some strategies for protecting against it.
How Sandwich Attack Happens
Sandwich Attack works by placing two transactions around a legitimate transaction in order to manipulate the outcome of the legitimate transaction. The first transaction is a small transaction with a high gas fee that aims to clog the network and delay the execution of the legitimate transaction. The second transaction is then sent with a lower gas fee and is designed to manipulate the outcome of the legitimate transaction.
For example, let's say there is a decentralized exchange on a blockchain that allows users to trade cryptocurrencies. The exchange uses a smart contract that relies on an external price oracle to determine the exchange rate between two cryptocurrencies. An attacker can use Sandwich Attack to manipulate the exchange rate for their own gain.
The attacker starts by submitting a small transaction with a high gas fee, which clogs up the network and causes delays in processing other transactions. Next, the attacker submits a buy order for a large amount of cryptocurrency at a low price. This transaction is designed to execute at the same time as the legitimate transaction that someone else has submitted to buy the same cryptocurrency, but at a higher price. Finally, the attacker submits a sell order for the same cryptocurrency at a high price. This transaction is designed to execute after the legitimate transaction has executed, but before the price oracle updates the exchange rate.
As a result, the attacker is able to buy the cryptocurrency at a lower price and then sell it at a higher price, making a profit at the expense of the legitimate trader.
Another Example for a clear understanding:
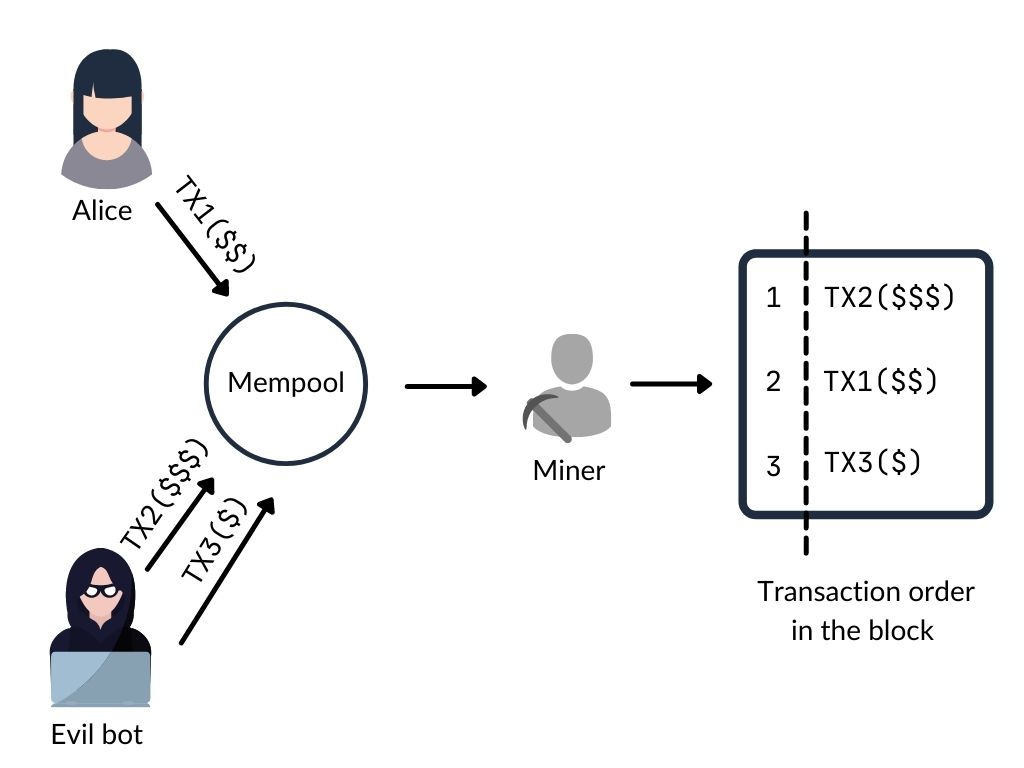
let's say that Alice wants to buy 1 Bitcoin on a cryptocurrency exchange. She places a buy order for 1 Bitcoin at a price of $50,000. However, before her buy order is processed, an attacker places a sell order for 1 Bitcoin at a price of $49,000. This sell order slows down the processing of Alice's buy order, giving the attacker more time to manipulate the market.
After the attacker's sell order is processed, they quickly place a buy order for 1 Bitcoin at a price of $50,500. This buy order is placed just after Alice's buy order is processed. This causes the price of Bitcoin to rise, so the attacker can sell their Bitcoin at a higher price, making a profit.
In this scenario, the two fake transactions are the attacker's sell order and buy order. They are used to manipulate the market and profit at Alice's expense. The legitimate transaction is Alice's buy order, which is sandwiched between the two fake transactions.
To protect against a Sandwich Attack, blockchain developers can use measures such as higher transaction fees, more secure code, and more complicated ways of determining prices. It's also important for users to be cautious and investigate any suspicious transactions before proceeding with a trade or transaction.
Protecting Against Sandwich Attack
One approach to protect against Sandwich Attack is to increase the gas fees for transactions. Gas fees are the fees paid to miners to process transactions on the blockchain. By increasing the gas fees for transactions, developers can make it more expensive for attackers to carry out Sandwich Attack.
Another approach is to use a more secure and randomized price oracle. A price oracle is a trusted source of information about the current price of an asset. By using a more secure and randomized price oracle, developers can make it more difficult for attackers to predict the outcome of a transaction and manipulate prices.
Finally, developers can incorporate other security measures into the smart contract code. For example, they can use multi-signature wallets to require multiple parties to sign off on a transaction, or they can implement time-based locks to prevent transactions from executing too quickly.
what you can do to protect yourself from becoming a victim.
Here are a few tips:
Research the cryptocurrency exchange or platform you are using: Before using any cryptocurrency exchange or trading platform, do some research to make sure it's reputable and has a good track record of security. Check reviews from other users and look for any red flags or warning signs.
Keep an eye on the market: Pay attention to the price movements of the cryptocurrency you want to trade. If you notice sudden and unexplained price changes, be cautious and investigate further before making any transactions.
Check the transaction history: Before making a trade or transaction, review the transaction history for any suspicious activity, such as transactions that seem out of place or appear to be part of a Sandwich Attack.
Use two-factor authentication: Enable two-factor authentication on your account to add an extra layer of security to your transactions. This can prevent unauthorized access to your account and help protect your assets.
Set price alerts: Some cryptocurrency exchanges and trading platforms offer price alerts that notify you when the price of a cryptocurrency reaches a certain level. Setting up price alerts can help you monitor the market and react quickly to changes.
Be cautious with high-value trades: If you're making a high-value trade or transaction, be extra cautious and take extra steps to verify the transaction. Consider splitting the trade into smaller transactions to reduce the risk of loss.
Conclusion
Sandwich Attack is a sophisticated type of transaction manipulation attack that can be used to make money illegally at the expense of legitimate traders. To prevent this type of attack, blockchain developers can implement measures. By doing so, they can help protect the integrity of the blockchain and ensure that legitimate transactions are not manipulated by attackers.
