From Cryptography to Voting: The Wide-Ranging Applications of Zero-Knowledge Proofs.
Zero Knowledge Proofs
what is Zero-knowledge proofs ?
Zero-knowledge proofs (ZKPs) are a type of cryptographic protocol that allows one party to prove to another party that a statement is true, without revealing any information about the statement itself.
In other words, ZKPs allow the prover to convince the verifier of the truth of a statement without revealing any additional information about that statement. This can be useful in situations where it is important to prove the authenticity of a statement or the possession of a secret, but where it is not necessary to reveal the actual contents of the statement or secret.
The concept of zero-knowledge proofs was first introduced in the 1980s by MIT researchers Shafi Goldwasser, Silvio Micali, and Charles Rackoff.
Here's an example to help illustrate the concept:
This example illustrates how ZKPs can be used to enable one party (Alice) to prove a statement (that she is over 18) to another party (Bob) without revealing any additional information about the statement (her actual age).
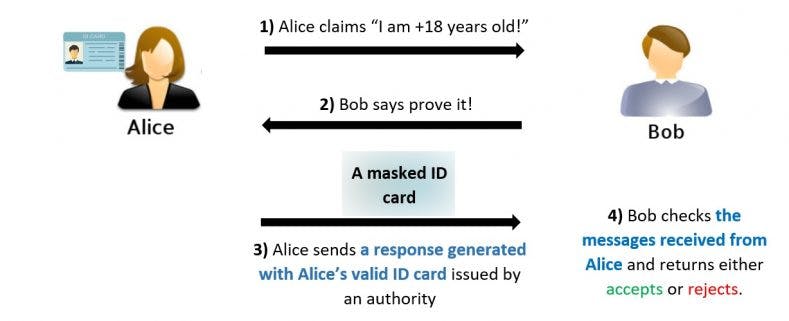
Here is an example of how zero-knowledge proofs (ZKPs) might be used to enable Alice to prove her age to Bob without revealing her actual age:
Bob asks Alice to prove that she is over 18 years old. Alice agrees, but does not want to reveal her actual age to Bob.
Alice and Bob engage in a series of interactions in which Alice provides various pieces of evidence to support her claim that she is over 18. This might include, for example, a government-issued ID that has been verified by a third party.
Bob checks the evidence provided by Alice to make sure it is authentic and verifies that it supports Alice's claim that she is over 18.
If Bob is satisfied that the evidence provided by Alice is sufficient to support her claim, he can be convinced that Alice is over 18 without actually learning her actual age.
Applications in ZKPs
Here are a few examples of potential applications of zero-knowledge proofs (ZKPs), along with brief descriptions of how they might work:
Cryptography: ZKPs can be used to prove the authenticity of a message or the possession of a secret without revealing the secret itself.
For example Alice might want to prove to Bob that she knows the secret password to a locked door, but she doesn't want to reveal the actual password to Bob. Alice can use a zero-knowledge proof to convince Bob To do this, Alice and Bob could engage in a series of interactions in which Alice provides various pieces of evidence to support her claim (such as correctly answering questions about the password), but Bob is not able to learn the actual password from these interactions.
Digital identity: ZKPs can be used to enable individuals and organizations to control their own digital identity and the data associated with it, and to use this identity to interact with the digital world in a secure and private way.
For example, Alice might want to prove to Bob that she is over 18 years old, but she doesn't want to reveal her actual age to Bob. Alice can use a zero-knowledge proof to convince Bob that she is over 18 without revealing her actual age. To do this, Alice and Bob could engage in a series of interactions in which Alice provides various pieces of evidence to support her claim (such as a government-issued ID that has been verified by a third party), but Bob is not able to learn Alice's actual age from these interactions.
Supply chain management: ZKPs can be used to enable secure and transparent tracking of goods as they move through the supply chain, without revealing sensitive information about the goods or the parties involved.
For example, Alice might want to prove to Bob that a particular shipment of goods is genuine and has not been tampered with, but she doesn't want to reveal the specific details of the goods or the parties involved. Alice can use a zero-knowledge proof to convince Bob that the shipment is genuine without revealing any additional information. To do this, Alice and Bob could engage in a series of interactions in which Alice provides various pieces of evidence to support her claim (such as a tamper-evident seal on the shipment), but Bob is not able to learn the specific details of the goods or the parties involved from these interactions.
Voting systems: ZKPs can be used to enable secure and private voting systems, in which voters can prove that they have cast their vote without revealing how they actually voted.
For example, Alice might want to prove to Bob that she has cast her vote in an election, but she doesn't want to reveal how she actually voted. Alice can use a zero-knowledge proof to convince Bob that she has cast her vote without revealing how she voted. To do this, Alice and Bob could engage in a series of interactions in which Alice provides various pieces of evidence to support her claim (such as a receipt for her vote), but Bob is not able to learn how Alice actually voted from these interactions.
Auction systems: ZKPs can be used to enable secure and private auction systems, in which bidders can prove that they are willing to pay a certain price for an item without revealing their actual bid.
For example, Alice might want to prove to Bob that she is willing to pay a certain price for a particular item in an auction, but she doesn't want to reveal her actual bid to Bob. Alice can use a zero-knowledge proof to convince Bob that she is willing to pay the price without revealing her actual bid. To do this, Alice and Bob could engage in a series of interactions in which Alice