Table of contents
Hashing is Not Encryption because in encryption we can get the data after Decryption. but that's not the case with hash. Hashing and Encryption have different functions. Encryption includes encryption and decryption process
So what is Hashing ?
In short Hashing is a one-way process which changes data into the message digest or secure hash algorithm which is irreversible.
Hash function is a mathematical function which takes Arbitrary length of Numerical data and convert that into a fixed length numerical data. The Input can be of Any length but output will be of Fixed size. Based on the algorithm what we using to do that the output length will change.we have a concept of MD,SHA so based on what type of algorithm we use we will be getting a different set or length of hash value.
The Amazing part is you can give a huge chunk of data(eg. 5GB of data)or smallest data you will get a fixed Hash Value. doesn't matter how many times you do that with same algorithm it will get the same hash value.
For the same input we will be getting the same hash value every time.
Another thing is that if you have made a small change in your text it will change your entire hash value .even if you change an alphabet in your text to capital to small letters it will change the hash value completely every time.
You cannot get the actual input from the Hash value, which means Reverse is not possible. it is almost impossible to get the data back once you get the hash value. because when you do hashing you will loose lot of data. suppose you input data in GB's the output will be in bits,so it is impossible to get your data back.
One more important thing is for two different messages you will be having two different hash values. it will never be same. if it is same then it will create collision.
There are different algorithms available one of them is MD(Message Digest)and we have different versions of it. MD1,MD2,MD3..........MD6,latest is MD6. people are not using MD5 so now they are moving towards SHA(Secure Hash Algorithm) which is build my National Security Agency (NSA) we also have different versions for SHA, they are SHA0,SHA1,SHA2,SHA3.
SHA popular version are SHA-256 and SHA-512, this 256 and 512 represent the output bit values. if we are using SHA-256 it will be having output as 256 bits and if you use SHA-512 it will be output 512 bits.
we can use hash values in multiple places for security and we can use hash values in blockchain as well.
where we use Hashing algorithm in Blockchain?
lets have a look at a Block, because that's where we'll see its use.
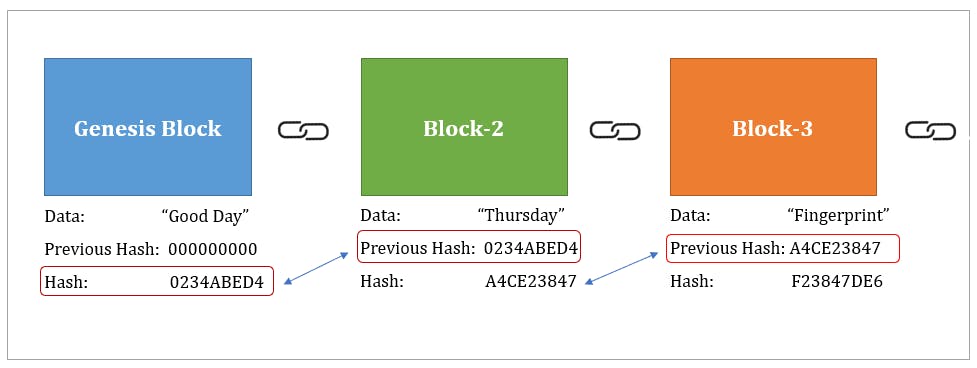
so it is our blockchain,here Genesis is the first block,then we have our data,then previous hash and Hash.
block no -tells what number of block it is 0, 1,2,3,etc.where 0th is the Genesis block.the origin block in the blockchain.
data - it represents the transactions.
hash- as you can see every block is connected so it is important that these blocks identifies each other if we also want to identify a block,then we should be able to identify it. so it is Allocates a hash value,using SHA256 algorithm. SHA256 algorithm convert's a data in an irreversible encrypted form.
previous hash-here in the image there are 3 blocks, in Genesis block we got the hash value by using SHA256 algorithm,now that generated hash is getting connected or pointed by block-2. the block-2 is able to point to genesis block through this previous hash. hash value of genesis block and previous has value of block-2 is same. similarly with block-3 its previous hash value is same as hash value of second block-2.

